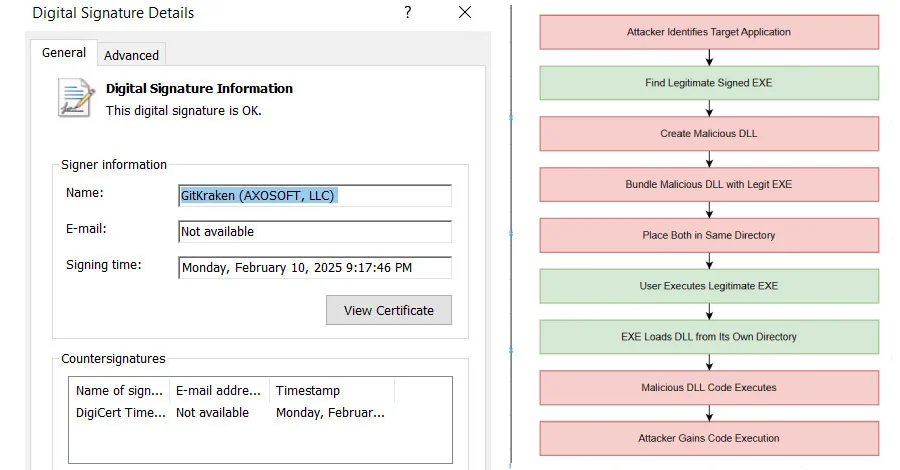
A malware campaign exploiting a DLL side-loading vulnerability has been uncovered, targeting sectors such as finance and supply chain. The attacks utilize a malicious version of libcares-2.dll alongside a renamed, signed executable of ahost.exe, which is associated with GitKraken's Desktop application. This technique allows cybercriminals to evade traditional security measures by executing unauthorized code.
Security experts at Trellix detailed the range of malware being distributed, including Agent Tesla, CryptBot, and XWorm. The campaign has been observed using various deceptive file names, such as "Fatura da DHL.exe" and "PO-069709-MQ02959-Order-S103509.exe," to lure users into opening the malicious files, often themed around invoices and requests for quotes.
Targets have been identified across multiple languages, indicating a specific regional focus in the attacks. The report emphasizes the increasing risk associated with DLL sideloading attacks, highlighting how legitimate software can be exploited to facilitate remote access and data theft.